Project background
On February 10, 2010, the 122th plenary session of the International Olympic Committee (IOC) was held in Vancouver, Canada, choosing Nanjing, China as the host city of the second session of Summer Youth Olympic Games in2014 by voting. Nanjing Youth Olympic Games is another important Olympic games for China after Beijing Olympic Games in 2008. The game aims to gather all the gifted young athletes worldwide to organize a competitive events with high level. In addition, it still should be an educational project in the Olympic spirit and offer young people a healthy lifestyle through athletics.
The second Youth Olympic Games torch was lit on Beijing time April 30, 2014 afternoon in Athens, Greece. The torch relay of the second Youth Olympic Games began on April 30. Network APP for the torch relay of Nanjing Olympic Games is used for network torch relay with multivariate and innovate interact style, and spread the Olympic flame to the whole world. It is the first time for the torch relay to use a virtual way.
Because it is the first time to use virtual network for torch relay, the high availability of the IT support system would provide important guarantee for torch relay. The bottom IT system of the Youth Olympic torch network involves three WEB servers and 2 DB server. Concrete structure is as follows:
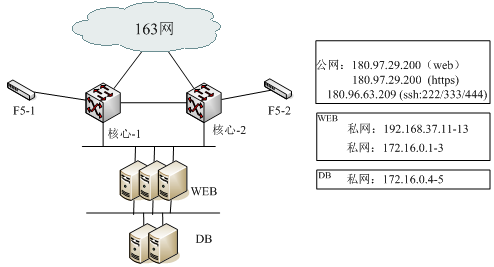
The disaster backup of aforesaid core WEB applications and database is an important factor for the stable running of the system. It ensures the smooth torch relay at any cases and set up good international image. It makes this Olympic Games a sporting event with the highest information level, best information service and best communication service capacity so that realize "wisdom youth Olympic" in the true sense. However, traditional solutions, such as cold standby and magnetic tape handler have many defects and could not realize real and fast recovery of data and business in time. The target of disaster backup and the management of continuous applications should at least include several aspects as follow:
Ensure business continuity. Recovery time objective RTO approximately equal to 0 so that the system can quickly restore business system and provide service for the external after a system failure .
Resist catastrophe. Realize offside disaster recovery to resist all kinds of large-scale natural calamities and man-made misfortunes. It is easy to operate disaster drills.
Trust its safety. Disaster backup system will contact and get all data of the user's with no reservations. Resolutely put an end to the back door, especially for the data and departments with confidentiality requirement because the security of data is more important.
Be simple and easy to use. Simplicity is a necessary condition for the construction of disaster backup software, otherwise, the company spends money while no one can make a good use of it.
TCO is reasonable. It should be easy to use and maintain with easy extension and promotion. Do not simply pursue cheap price. It is better to be a system suitable for the habit of Chinese.
Requirement instructions
Considering the importance and restrict demands of the youth Olympic torch network, it is a good solution to protect the related data with disaster backup software. In other words, make use of the software on the servers to realize remote backup through IP network. Realize disaster backup for the data and zero data loss and can recover data to any time point in the history which is the function of CDP protection.
It requires that the backup software should support unified monitoring and configuration of Chinese interface by means of web. The software is required to support several operating systems (at least Windows and Linux ).It should realize protection and backup of data, files and several kinds of database. At the same time realize real time protection of application and remote disaster recovery and take over the application when it is unusual. Catch byte-level increment through bypass mode. Through the log function of backup software, make corresponding policy processes for data backup including start time, storage path, flow control, backup mode, state management and so on and then copy the update operation of data to the local or remote backup system. When the local backup system breaks down, data could be recovered from the offside backup system.
I2 software adopts advanced asynchronous real-time data replication and immediately transfer the byte-level changes on all servers to the target server through network rather than the whole document or mirror of the disk. So it has the lowest impact on the performance of the server and network bandwidth. Once the target server takes over the service, users do not need to recover data and can activate the system in the shortest time,. Then the target server provides service for the external.
I2soft solutions can really realize real-time data protection with lowest cost and protect the real time, completeness and consistency of data to the utmost extent. Business data is one of the most precious property for the user. The loss of data is the profit loss for the enterprise. So the protection of the business data is one of the main functions for the enterprise computing system. Disaster backup solutions of I2 software can realize the least loss and even zero loss.
In order to realize disaster backup for all systems in limited bandwidth, combine the specific requirement and take reliability high efficiency and safety as the first. This solution adopts i2 software and describes the design and planning in detail and specific implementation details.
Solution instruction
According to the current practical environment and requirements referred above, i2 software provides the following solution. The topological graph is as follows:
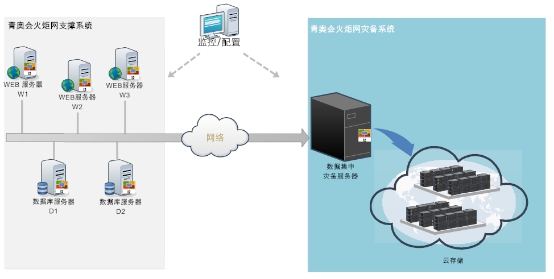
As the above solution, i2 software is installed on the related source and target servers. It aims mainly at real time protection of related data and realizing the real-time copy protection of data between the two servers. When the source server is unusual, recover the data quickly. Detailed instruction is shown as follows:
Production Servers: There are 5 servers on which I2software clients are installed. By doing so, i2software can backup directoryin real time and continuouslyprotect related data through I2CDP. When abnormal situation occurs, disaster recovery system deployed on cloud platform of Telecom immediately provides rapid recovery service of data, which means i2software rapidly recover data to selected server and guarantee the data availability.
The disaster recovery center are virtual servers, and i2soft server side modules are installed on these virtual servers, which centrally protect the data of production system. Production system and disaster recovery system are connected by a private network address(172.16.0.*), and the disaster recovery system of Telecom cloud platform receives the data sent from production system and provides the instant recovery service of data under abnormal condition.
I2CDP can make a complete record for the data change in the server, providing snapshots at each time point and complete CDP recovery. When something wrong happended to the data source, it can restore the data at any time point.
All the configuration and monitoring can be realized through disaster recovery machine on the web, such as disaster congfiguration, traffic monitoring, restoration, etc. Control machine can be of any server in the grid, on which I2 server module is installedc and can be received by all the servers under management.
I2Scsft's byte-level data capture can greatly reduce the amount of data transfer volume, thus perfectly realizing data replication in the limited bandwidth and poor network environment.
With regard to system expansion, when there is new system to protect, all you need to do is install I2Soft module in it without purchasing isomorphic hardware or other disaster modules.
